Docker & Container Security – Penetration Testing on Docker and Container

Penetration Testing on Docker and Container
Some key commands for penetration testing Docker and container security, categorized for various stages of the process:
Enumeration and Information Gathering:
- Docker Daemon Information:
docker version (Check Docker version and features)
docker info (View detailed information about the Docker daemon)
ps aux | grep dockerd (Identify processes associated with the Docker daemon)
- Docker Socket Permissions:
stat /var/run/docker.sock (Check permissions on the Docker socket)
- List Running Containers:
docker ps -a (List all containers, including stopped ones)
docker ps (List running containers)
docker inspect <container_id> (Get detailed information about a specific container)
- Image Analysis:
docker images (List available Docker images)
docker history <image_name> (View the history of an image)
Vulnerability Scanning:
- Built-in Docker Scanner:
docker scan <image_name> (Perform a basic vulnerability scan on an image)
- External Vulnerability Scanners:
anchore engine analyze –image <image_name> (Use Anchore Engine for a more comprehensive scan)
snyk docker image analyze <image_name> (Utilize Snyk for vulnerability analysis with additional features)
Exploitation and Privilege Escalation:
Disclaimer: These commands are for educational purposes only and should never be used on systems without explicit permission.
- Docker Socket Exploitation (if exposed):
Tools like socat or custom scripts can be used to exploit vulnerabilities in the Docker daemon if the socket is exposed and writable. (Research is required for specific commands)
- Container Privilege Escalation:
Tools like docker-vuln-scan or exploit databases can be used to identify potential vulnerabilities within the container image.
Techniques like exploiting misconfigurations, gaining access to the host through volume mounts, or leveraging container escape vulnerabilities might be attempted. (Consult security resources for ethical exploitation methodologies)
Post-Exploitation and Persistence:
- Container File System Exploration:
docker cp <container_id>:/path/to/file /host/path/to/folder (Copy files from the container to the host)
- Container Process Enumeration:
docker exec -it <container_id> ps aux (List processes running inside the container)
- Maintaining Access (Unethical and illegal):
Techniques like planting backdoors or modifying container startup scripts for persistence are unethical and illegal. Pen-testers should focus on identifying vulnerabilities and reporting them responsibly.
Nmap:
Scan Docker host for open ports:
root@ubun2004:/home/ubuntu/Downloads# docker pull instrumentisto/nmap
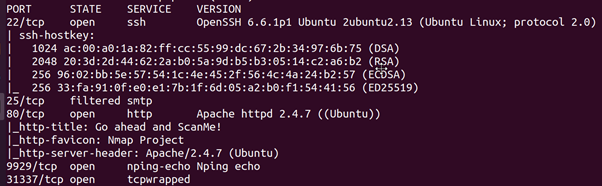
root@ubun2004:/home/ubuntu/Downloads# docker run –rm -it instrumentisto/nmap -A -T4 scanme.nmap.org
Docker Bench Security:
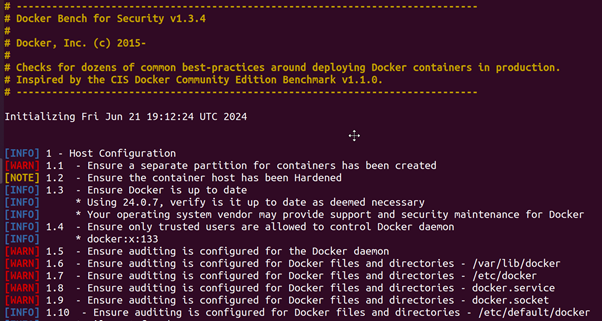
Run Docker Bench Security to check for common security best practices:
root@ubun2004:/home/ubuntu/Downloads# docker pull docker/docker-bench-security
root@ubun2004:/home/ubuntu/Downloads# docker run -it –net host –pid host –userns host –cap-add audit_control \
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
-v /var/lib:/var/lib \
-v /var/run/docker.sock:/var/run/docker.sock \
-v /usr/lib/systemd:/usr/lib/systemd \
-v /etc:/etc –label docker_bench_security \
docker/docker-bench-security
Trivy:
- Scan Docker images for vulnerabilities:
root@ubun2004:/home/ubuntu/Downloads# docker pull bitnami/trivy
root@ubun2004:/home/ubuntu/Downloads# docker run –rm –name trivy bitnami/trivy –version
root@ubun2004:/home/ubuntu/Downloads# docker run –rm –name trivy bitnami/trivy image alpine
Metasploit:
- Perform penetration testing on Docker containers:
root@ubun2004:/home/ubuntu/Downloads# docker pull metasploitframework/metasploit-framework
OWASP ZAP:
- Perform security testing on web applications running inside containers:
zap.sh -daemon -port 8090 -host 0.0.0.0 -config api.disablekey=true -config api.addrs.addr.name=.* -config api.addrs.addr.regex=true
- Kali Linux:
Use various built-in tools in Kali Linux for penetration testing:
root@ubun2004:/home/ubuntu/Downloads# docker pull donaldrich/kali-linux
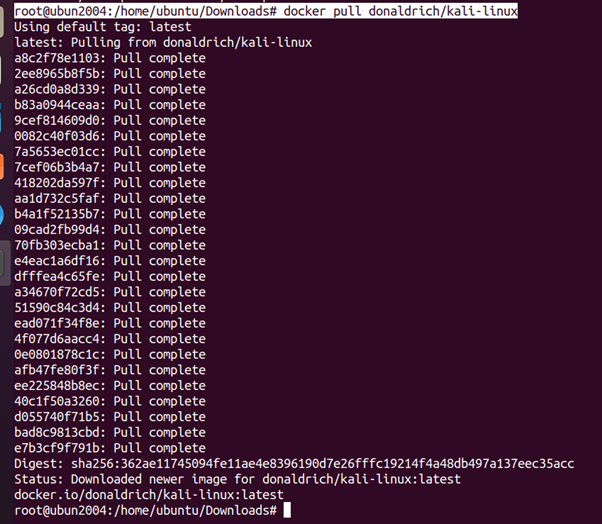
Burp Suite:
Intercept and modify HTTP/S requests:
burpsuite
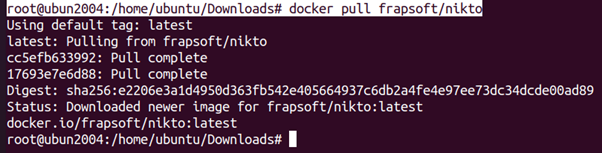
- Nikto:
Scan web servers running inside containers for vulnerabilities:
root@ubun2004:/home/ubuntu/Downloads# docker pull frapsoft/nikto
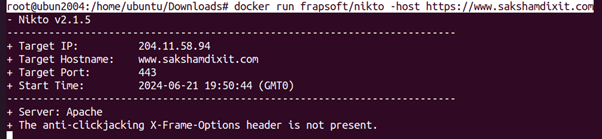
root@ubun2004:/home/ubuntu/Downloads# docker run frapsoft/nikto -host https://www.sakshamdixit.com
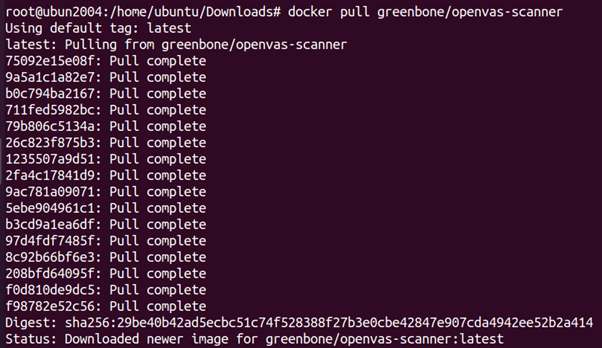
OpenVAS:
Perform vulnerability scanning on Docker hosts and containers:
root@ubun2004:/home/ubuntu/Downloads# docker pull greenbone/openvas-scanner
Additional Tools and Techniques:
- Network Sniffing: Tools like tcpdump or Wireshark can be used to capture network traffic between the Docker daemon, containers, and the host for potential credential leaks or sensitive information.
- Static Code Analysis: If the source code for the containerized application is available, static code analysis tools can be used to identify potential vulnerabilities within the codebase.
Remember:
- Ethical Hacking: Always obtain written permission before penetration testing any system.
- Understanding Risks: Exploiting vulnerabilities can have unintended consequences. Ensure you understand the risks before proceeding.
- Focus on Reporting: The goal of pen-testing is to identify vulnerabilities and report them responsibly for remediation.
By using these commands and techniques responsibly, you can effectively assess the security posture of Docker environments and identify areas for improvement.
@SAKSHAM DIXIT
